Kaspersky Blog Uefi

Your gateway to all our best.
Kaspersky blog uefi. My Products Subscriptions. This blog will delve into many of the advantages of becoming a UEFI Forum member from helping shape new market opportunities to meeting other innovators in the field. The UEFI bootkit used with the malware.
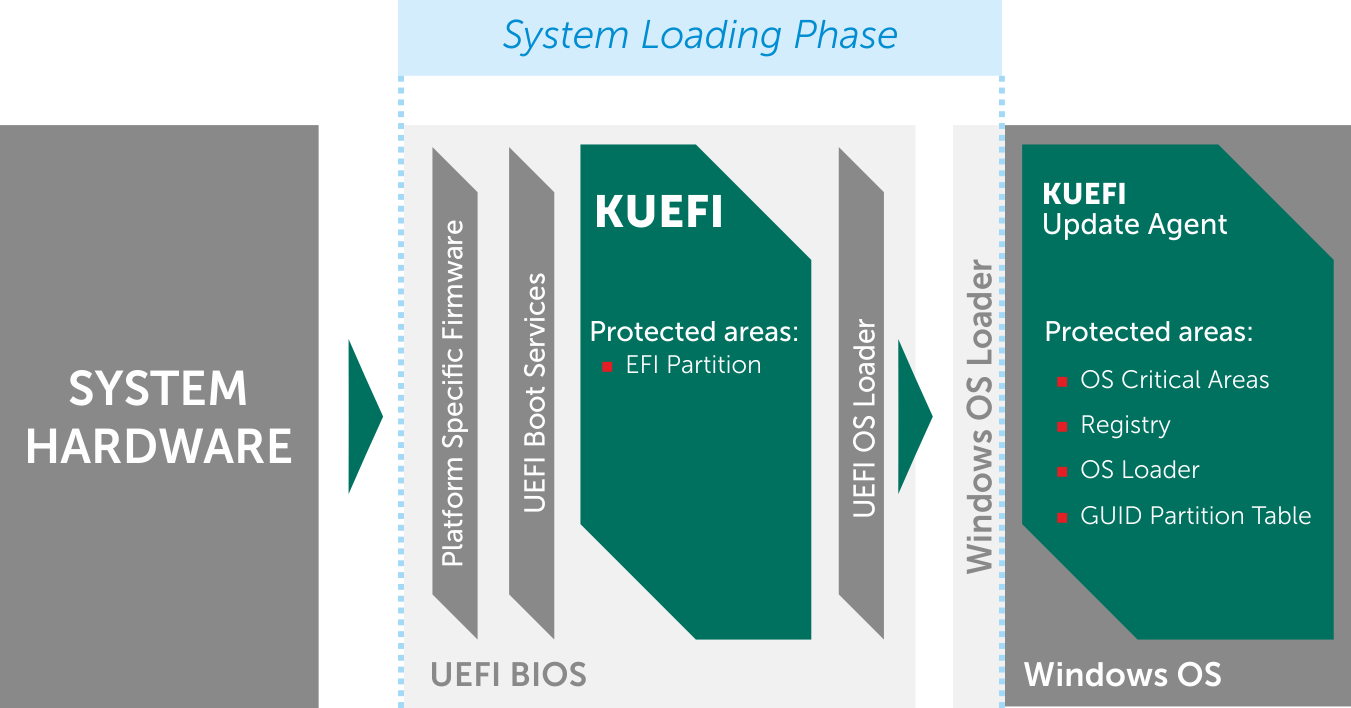
UEFI firmware is an essential part of a computer which starts running before the operating system and all the programs installed in it. Moreover it is stored not on the hard drive but on a chip on the motherboard. Kaspersky was unable to determine how the original UEFI code was altered but the team made some educated guesses based on a piece of 2015 UEFI malware.
The UEFI bootkit is being used as part of an Advanced Persistent Threat APT espionage campaign. The scanning technology identified a previously unknown malware in the Unified Extensible Firmware Interface UEFI an essential part of any modern computer device making it very difficult to detect and remove from the infected devices. My Products Subscriptions.
Get antivirus anti-ransomware privacy tools data leak detection home Wi-Fi monitoring and more. Se i criminali informatici modificano il codice UEFI potrebbero utilizzarlo per inviare malware al sistema della vittima. New Kaspersky Security Cloud.
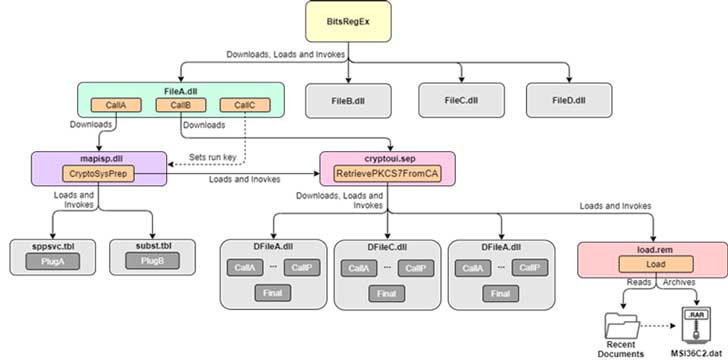
Kaspersky says it has spotted a customised firmware bootkit in the wild. The products key feature is that it starts running in the EFI environment even before the OS bootup process begins thus preventing any resident malware from loading. It has named the bootkit MosaicRegressor and said it is a variant of the HackingTeams VectorEDK bootkit that was leaked in 2015.
Access our best apps features and technologies under just one account. How to write an image of Kaspersky Rescue Disk in the ISO mode using Rufus. Select the USB drive.