Kaspersky Edr Requirements
While EDR extends the range of classical EPP its.
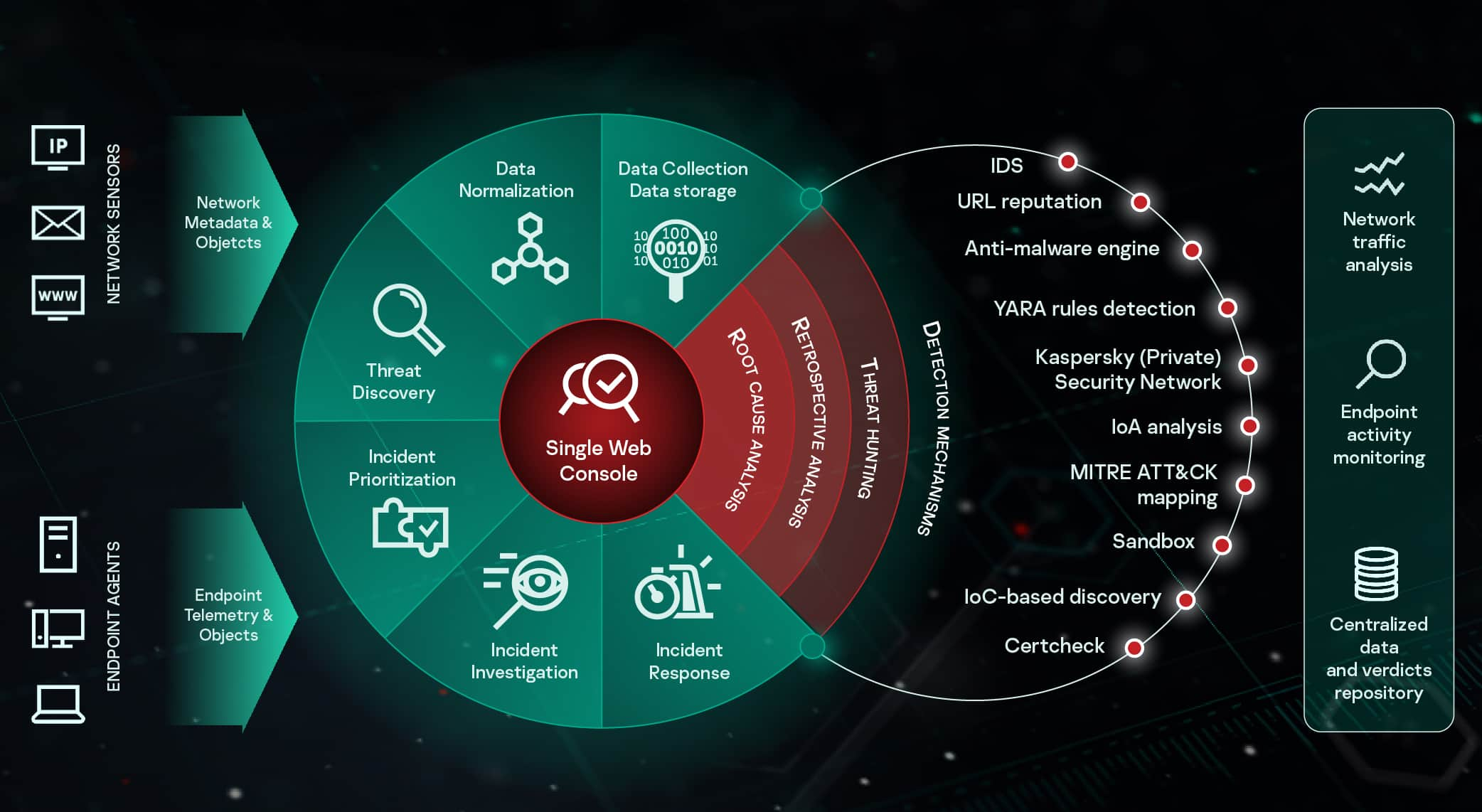
Kaspersky edr requirements. A single web interface enables real-time investigation and provides a historical database overview of activities even for endpoints which are not already on the network. With the help of Capterra learn about Kaspersky EDR its features pricing information popular comparisons to other Endpoint Detection and Response products and more. Kaspersky Lab Enters Endpoint Detection and Response Market with New Solution Available for Piloting.
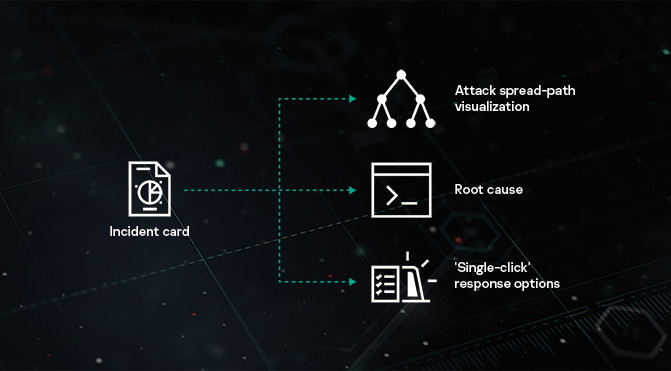
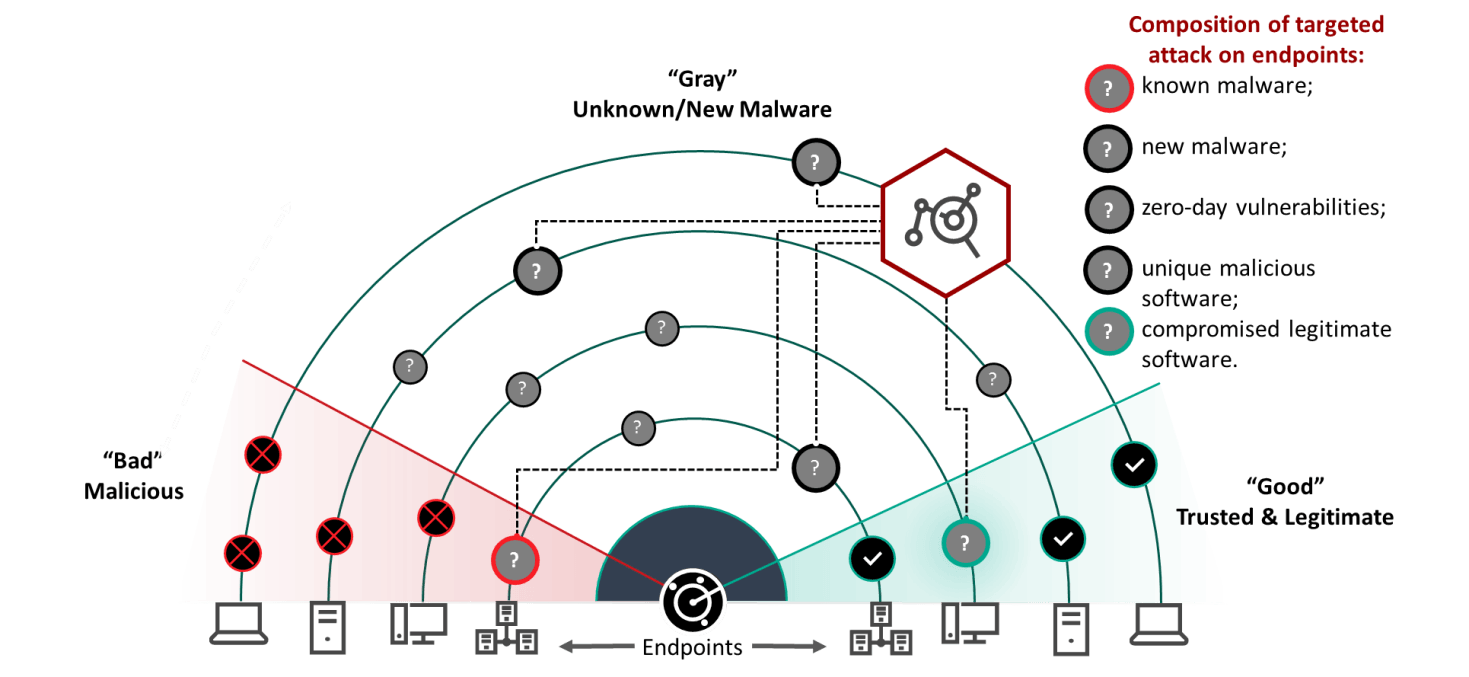
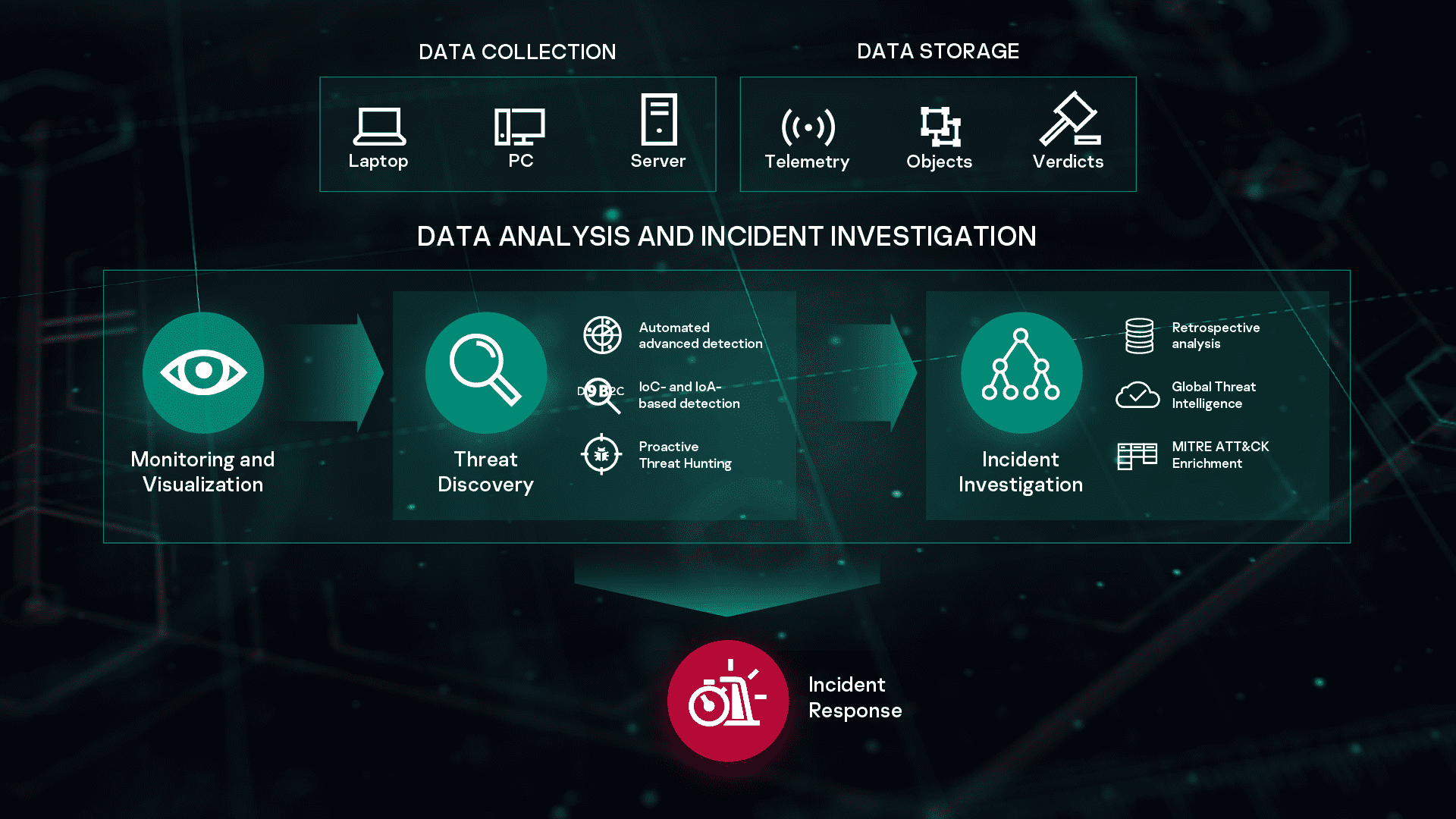
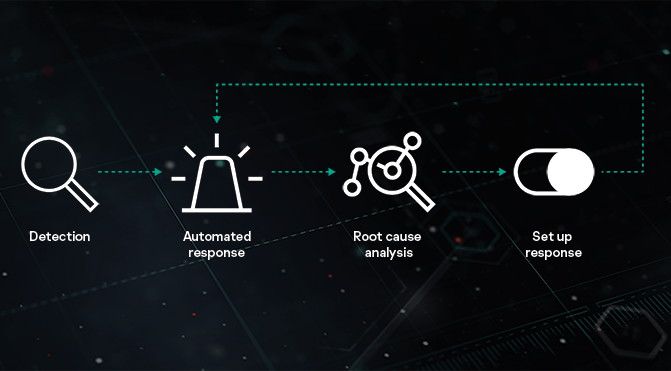
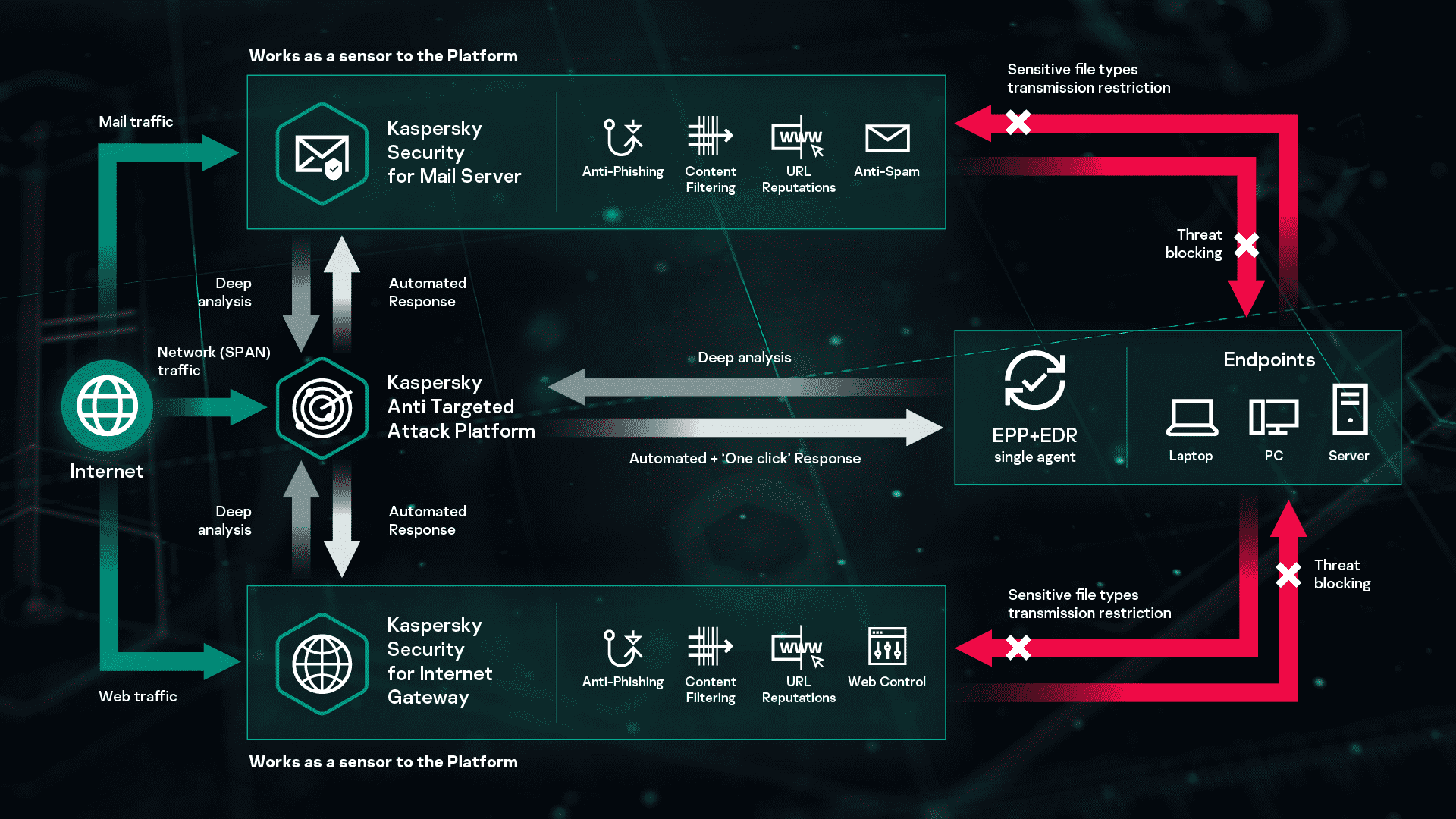
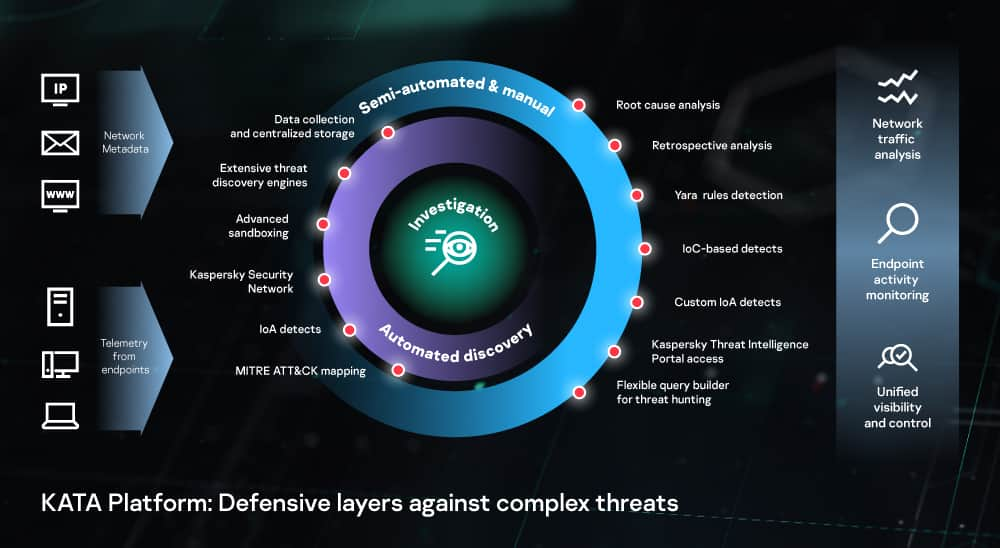
The solution can help strengthen your security against advanced threats by using automated response and simple root cause analysis with no additional overheads required. The persistent nature of advanced threats requires enterprises to reevaluate their cybersecurity ecosystems putting more focus to early identification of ongoing attacks and incident response. Kaspersky EDR can be absorbed into the Kaspersky Anti Targeted.
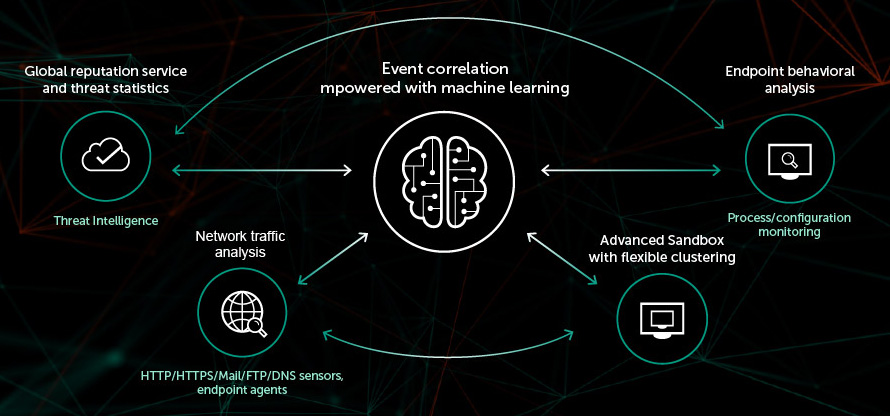
So create a checklist of what you need and. Editions Structure Pricing and Features. Real-time threat intelligence access via Kaspersky Security Network.
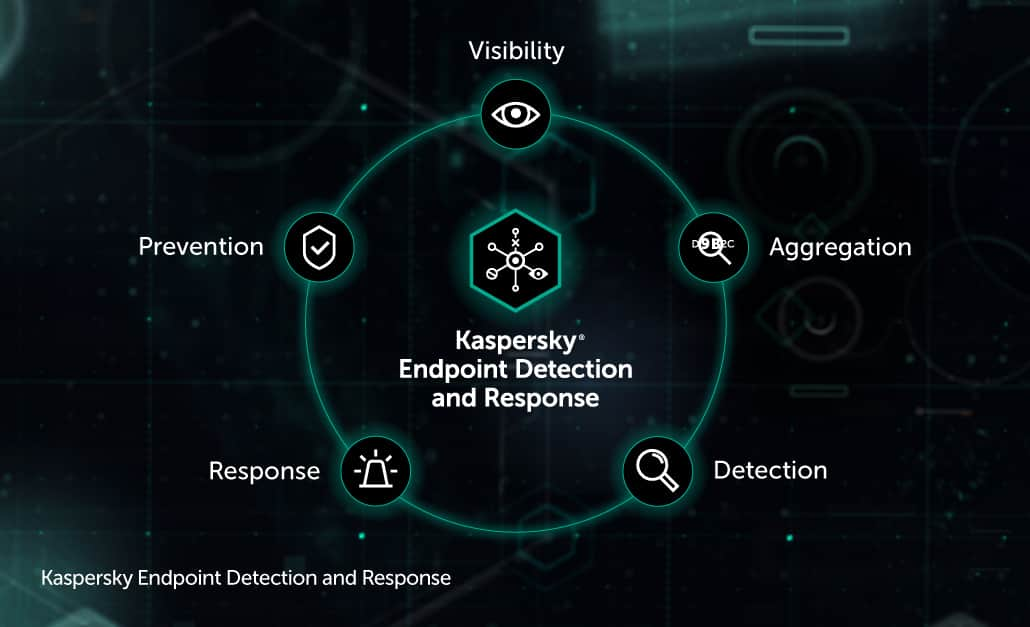
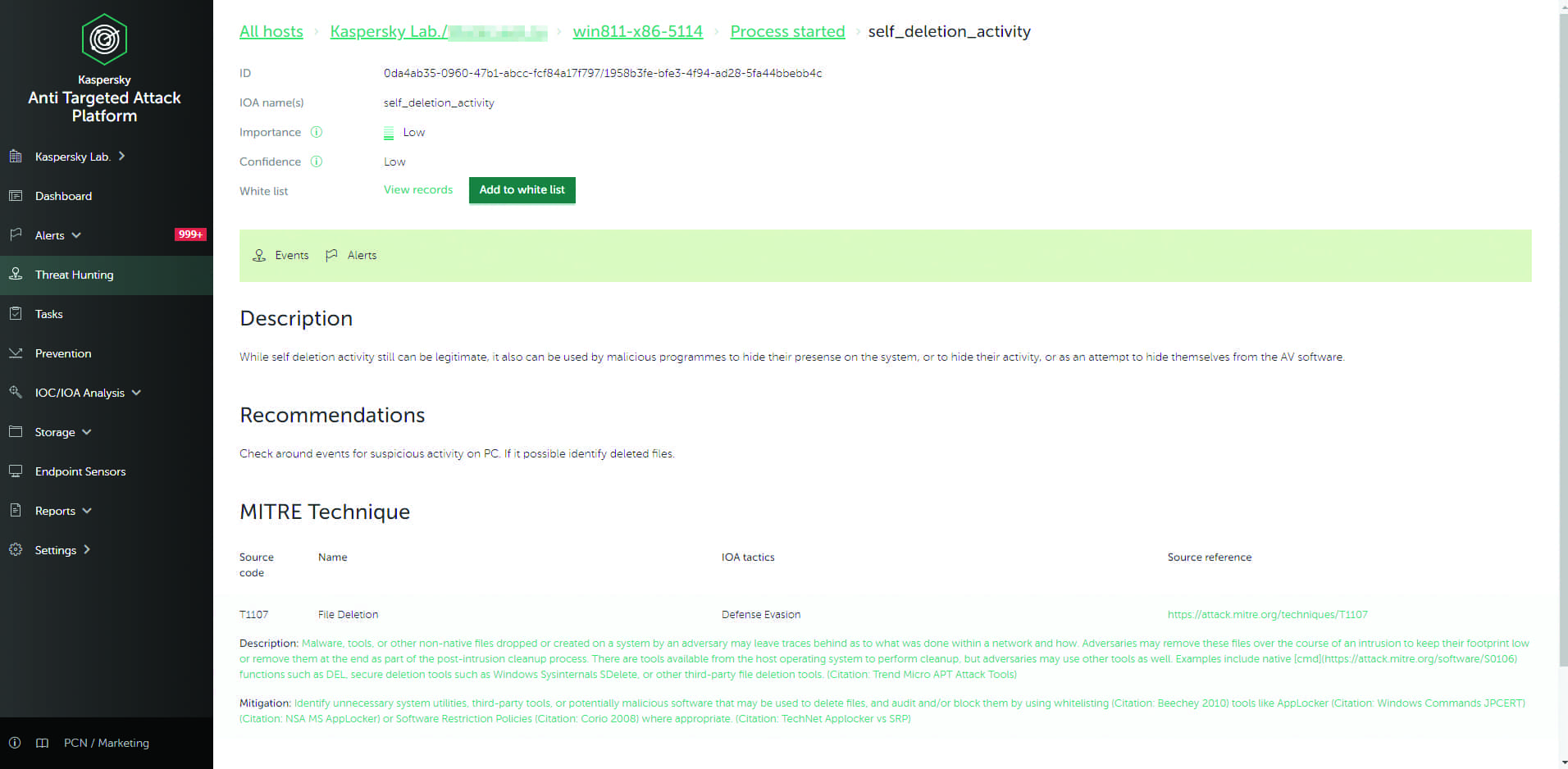
Up with their cyber security requirements and this expands the. Check out alternatives and read real reviews from real users. Kaspersky EDR is designed to defend endpoints against evasive threats and complex attacks and to provide IT securitySOC teams with a powerful tool for threat discovery in-depth incident investigation proactive threat hunting and a centralized response.
Still not sure about Kaspersky EDR. A 247 threat hunting service Kaspersky Managed Protection. Kaspersky Lab is a software business formed in 1997 in Russia that publishes a software suite called Kaspersky EDR.
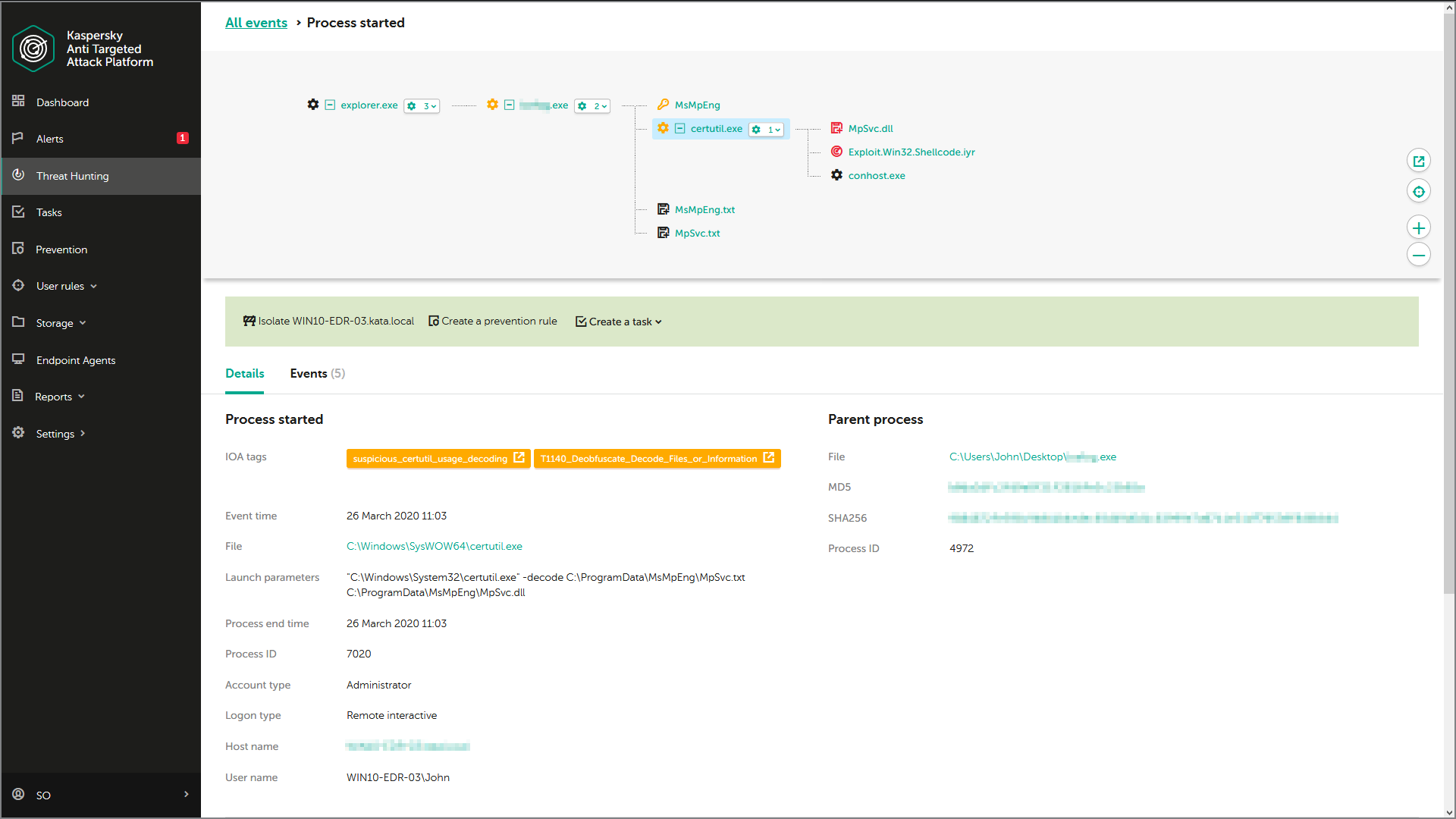
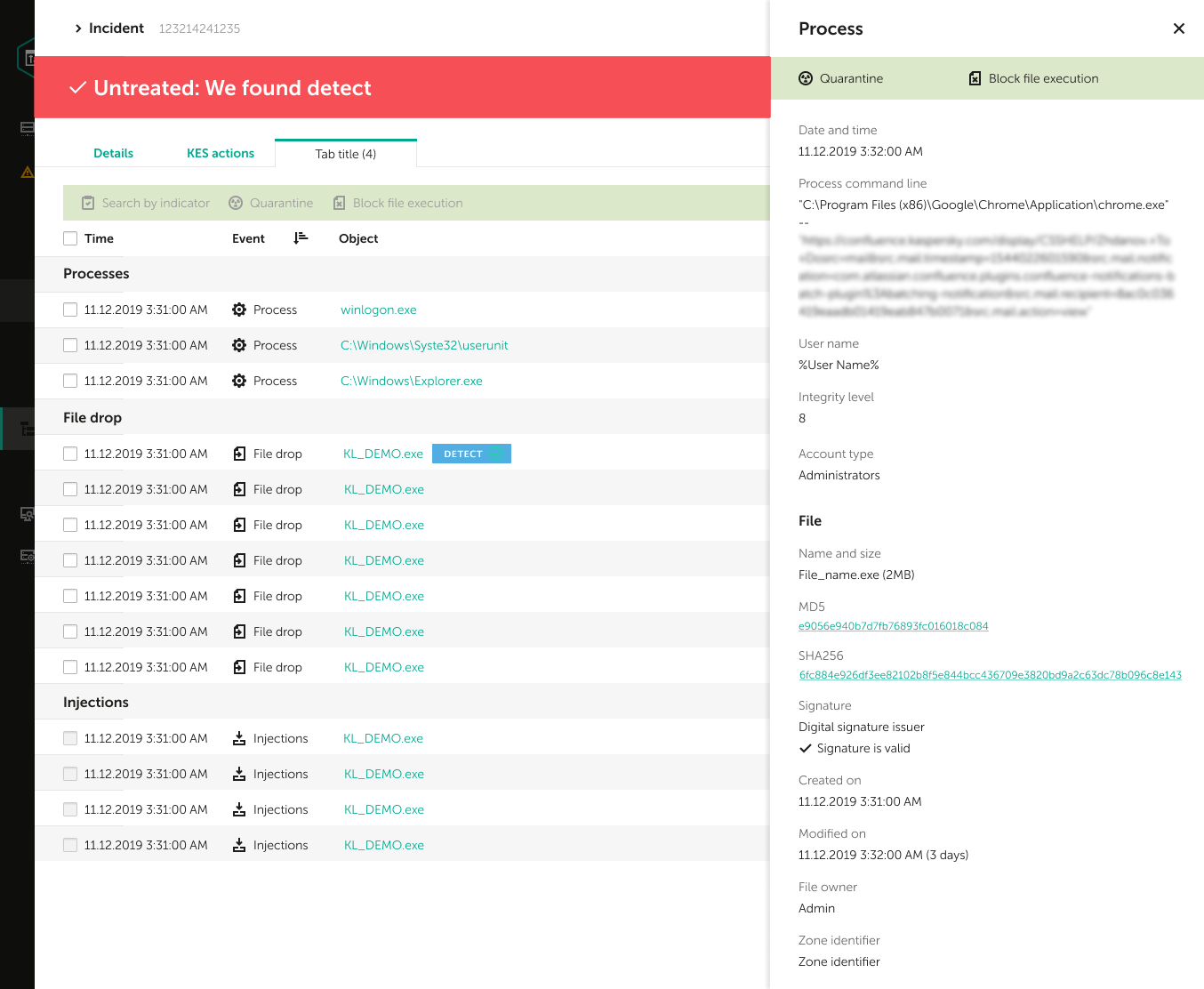
Consider upgrading from your traditional Endpoint Protection to Kaspersky Endpoint Detection and Response Optimum which can address modern cybersecurity threats without the cost of an expert. A processor that supports the SSE2 instruction set. Kaspersky EDR reduces the time needed for initial evidence collection provides full telemetry analysis and maximizes the automation of EDR processes cutting overall incident response times without the need to attract additional IT security resources.