Kaspersky Endpoint Security 11 Self Defense

Kaspersky Endpoint Security 111 for Windows is incompatible with AES encryption modules released for previous versions of Kaspersky Endpoint Security for Windows.
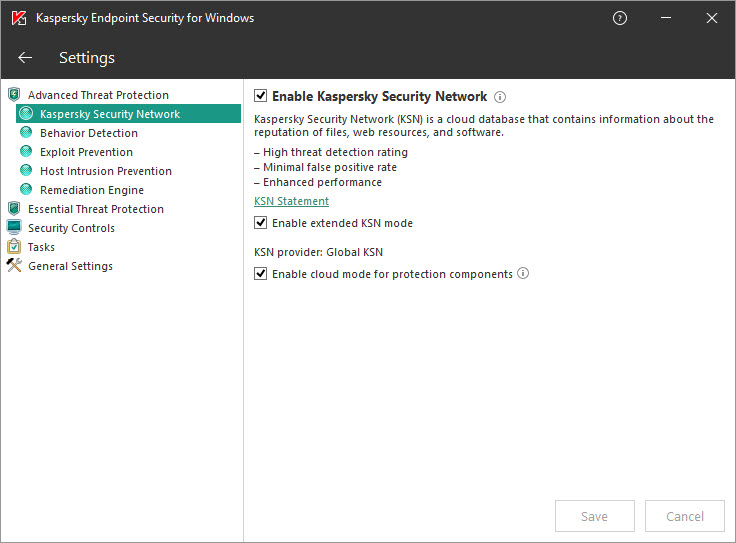
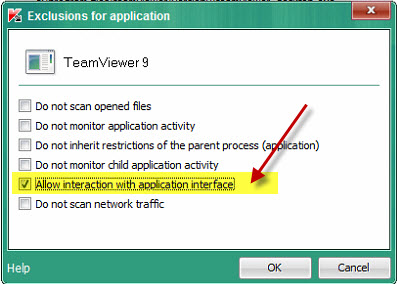
Kaspersky endpoint security 11 self defense. You decide - and well provide Kaspersky Endpoint Security for Business with adaptive protection automated threat defense and systems hardening for mixed environments. The Enable Self-Defense parameter is responsible for protecting the Kaspersky Endpoint Security processes in the computer system memory its files on the hard drive and its registry keys. Full version number is 11006499.
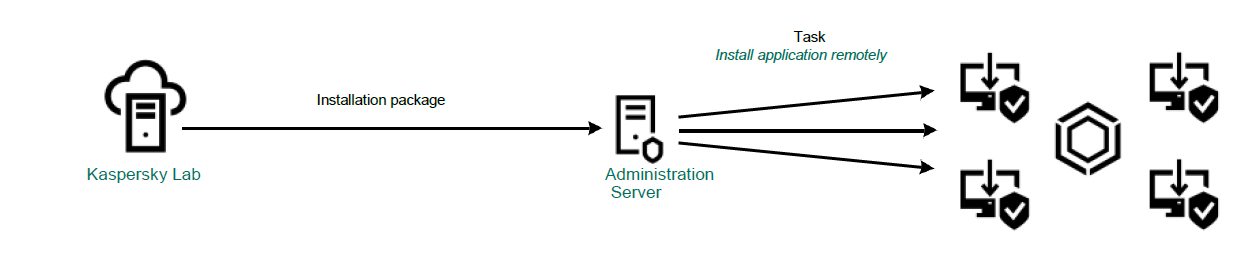
Select Access using Administration Server. During the endpoint roll-out process you can download all the necessary distributives directly from the management console. See Online Help for instructions.
Kaspersky Endpoint Security and Management The course prepares for planning deployment and maintenance of Windows network protection systems based on Kaspersky Endpoint Security and managed via Kaspersky Security Center. Kaspersky Endpoint Security 11 for Windows shows the notification that you need to close the processes that use the encrypted devices before the the application grants access to such devices. When preparing the Citrix XenDesktop master image with pre-installed Kaspersky Endpoint Security 1130 and the KSC Network Agent add exclusions of the following type to the configuration file.
System registry logs and memory processes from being modified or deleted. Application quarantine and trace files from being modified or deleted. To start the remote installation task through Kaspersky Security Center 10 and skip the check for incompatible software.
Activation data information about the key file or activation code that will spare you from activating the application if you reinstall it. Download the installer from the Kaspersky Endpoint Security 11 for Windows downloads page. Backup files files already checked by the application and put.
In some cases you may need to disable them. Extract the application installation files. Before cloning Self-Defense must be disabled on virtual machines that use vDisk.