Kaspersky Endpoint Security 11 Strong Encryption Vs Lite Encryption

Kaspersky Endpoint Security is a multi-layered endpoint protection platform based on true cybersecurity technologies.
Kaspersky endpoint security 11 strong encryption vs lite encryption. Kaspersky Endpoint Security Strong Lite Encryption endpoint security disable endpoint security comparison. See our list of best Endpoint Protection EPP for Business vendors. We do not post reviews by company employees or direct competitors.
We monitor all Endpoint Protection EPP for Business reviews to prevent fraudulent reviews and keep review quality high. Kaspersky Security 10 for Mobile.
Kaspersky Endpoint Security 11 for Windows Strong encryption 1111126. This tightly integrated solution combines fully scalable protection capabilities for physical virtual and cloud-based endpoints including desktops servers mobile devices and embedded systems. Open the properties for the Kaspersky Endpoint Security 10 policy.
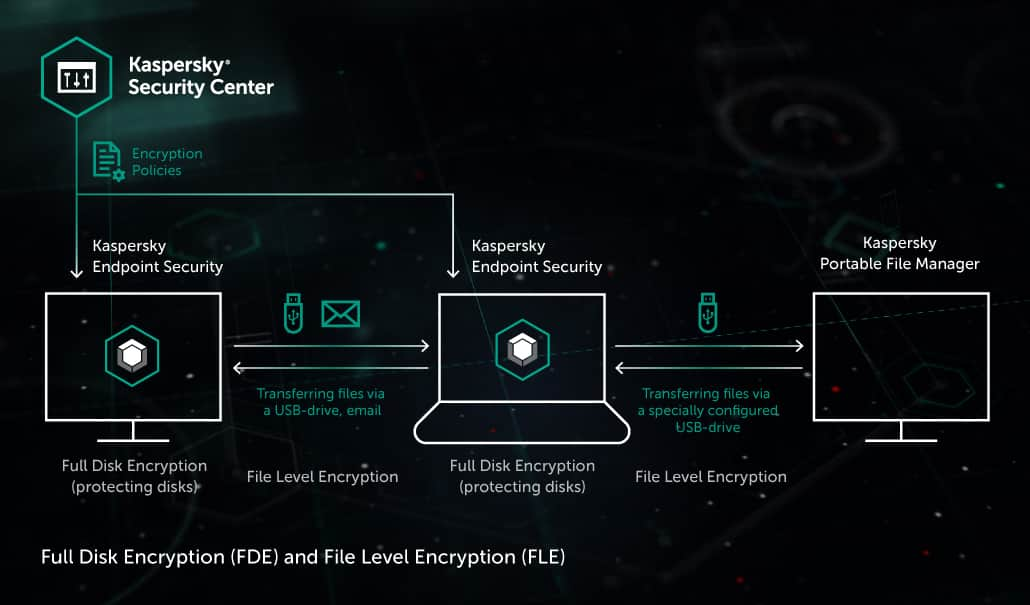
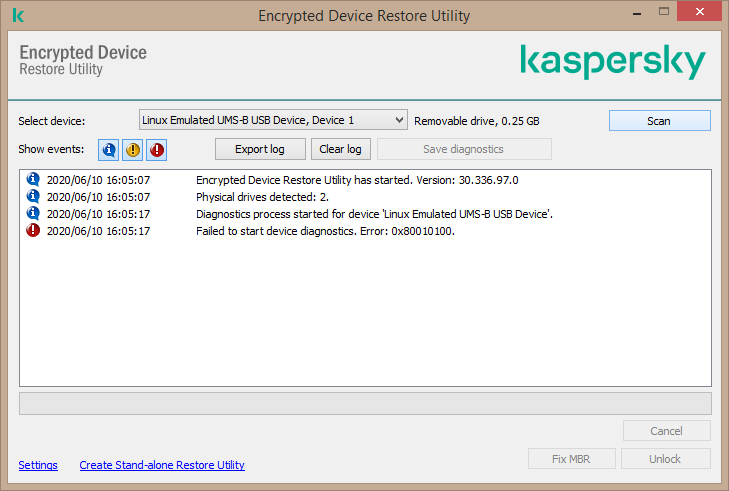
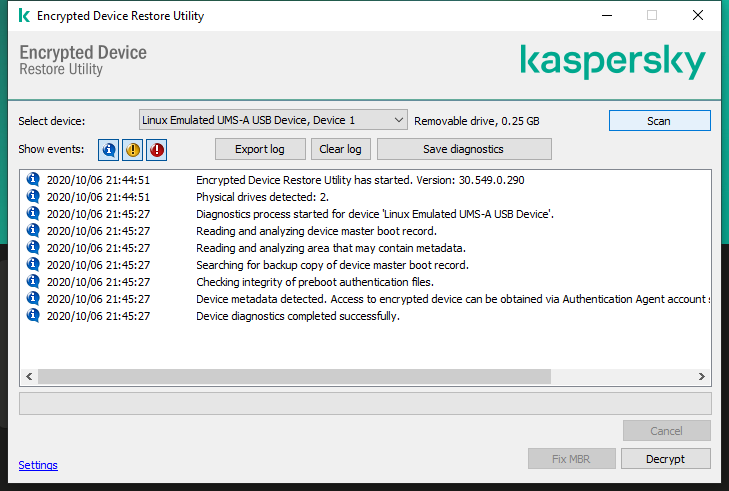
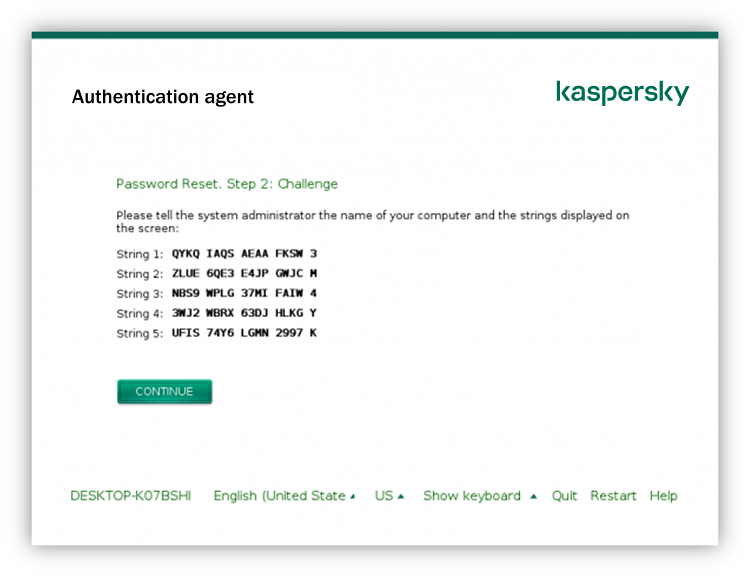
When installing an upgrade on a computer that has the AES Encryption Module installed the Kaspersky Endpoint Security 11 for Windows installer will automatically upgrade the Encryption Module and will install all libraries necessary for encryption if you are using a distribution package with the appropriate key length and are upgrading a supported configuration. Kaspersky Endpoint Security is a multi-layered endpoint protection platform based on true cybersecurity technologies. Limitations of full disk encryption support on devices with Kaspersky Endpoint Security 10 for Windows SP2 MR3 or SP2 MR4 installed id.
See our Kaspersky Endpoint Security vs. With Kaspersky Endpoint Security Cloud all you need to do is register an account and install the endpoint software and your business is. Limitations in Client-Side Caching CSC support while using encryption in Kaspersky Endpoint Security 11 for Windows for workstations only id.
Kaspersky Security Center System Health Validator SVH Application management plugins. Before you install Kaspersky Endpoint Security and activate encryption please make sure that other software with the same functions is not used on your. The administrator generates file lists in the policy according to file extensions or groups of extensions and folders contained on hard disks of client hosts.