Kaspersky Endpoint Security And Management Fundamentals Pdf

The risk of human error is minimized by systems hardening and by automating routine tasks such as Vulnerability and Patch Management OS and 3rd party software installation.
Kaspersky endpoint security and management fundamentals pdf. Microsoft Windows network administrators information security specialists technical support engineers presales engineers. It tells about those solutions that can help to protect a network of approximately up to 1000 endpoints in a single location. Kaspersky Labhas been positioned in the Leaders quadrant of the 2017 Gartner Magic Quadrant for Endpoint Protection PlatformsThe evaluation was based on the criteria for both completeness of vision and ability to execute.
Kaspersky Endpoint Security for Businessprovides robust protection based around one of the best anti-malware engines on the market. The ksn_txt file which you can view to look through the terms of participation in Kaspersky Security Network. The licensetxt file with which you can view the End User License Agreement.
The klcfginstmsi file for installing the Kaspersky Endpoint Security administration plug-in via Kaspersky Security Center. The course describes the Kaspersky Endpoint Security for Business solution that includes various Kaspersky Lab products. Heres how it protects your business.
2020 Independent Testing Awards In 2019 Kaspersky participated in 86 independent tests and reviews. Next Generation technologies and multilayered approach form the foundation of our high. Adaptive protection against advanced threats targeting your endpoints and users.
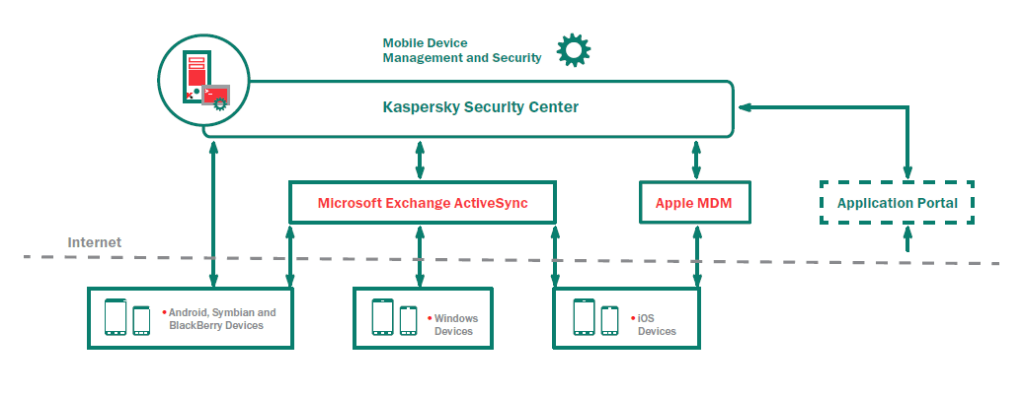
Kaspersky Endpoint Security and Management. Best Practices - Mobile Security. The course prepares for planning deployment and maintenance of Windows network protection systems based on Kaspersky Endpoint Security and managed via Kaspersky Security Center.
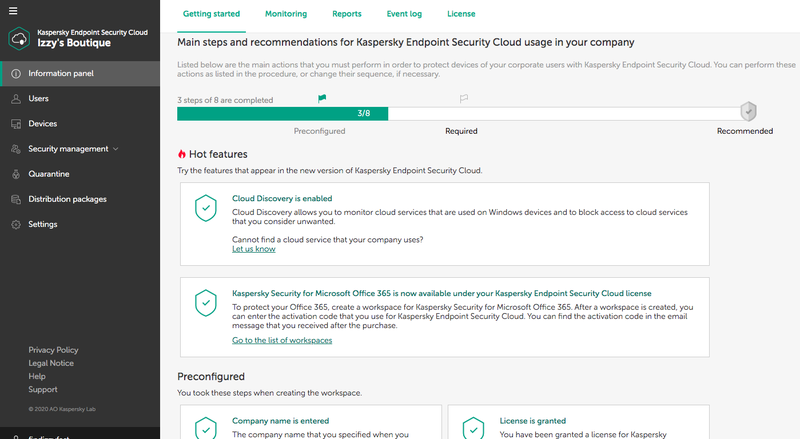
KSOS Management Console CompanyAccount. You have reached the max number of allowed answers Full Disk Encryption File Level Encryption Integrity Check Device Control 2. It tells about those solutions that can help to protect a network of approximately up to 1000 endpoints in a single location.