Kaspersky Endpoint Security Policy Greyed Out

Right-click in the policies field and select Group by column Inherited from the shortcut menu.
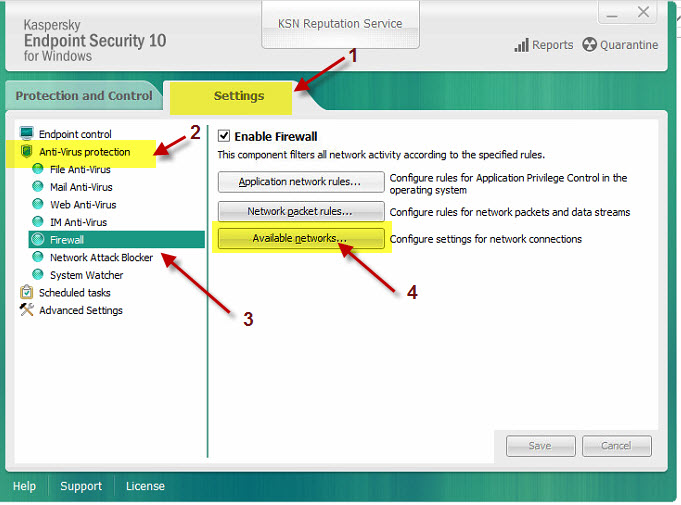
Kaspersky endpoint security policy greyed out. Kaspersky Endpoint Security for Windows harnessing cloud intelligence protects against ransomware exploits and advanced cyberthreats. Go to Advanced Setting s Application Settings. Kaspersky Endpoint Security for Business Select delivers agile security that helps protect every endpoint your business runs in a single solution with one flexible cloud-based management console.
In the cloud or on-premises. With more of your business operations going digital you need to protect every Windows or Linux server Mac laptop and Android mobile device. To view KSN statistics click Kaspersky Security Network in the top of the main window of Kaspersky Endpoint Security 10 for Windows.
Kaspersky Endpoint Security for Windows can only be removed through the installation wizard if it was installed locally. Powerful multi-layered protection against known unknown and advanced threats designed and built by the industrys leading security experts. Kaspersky Endpoint Security for Business backed by world-renowned threat intelligence provides unequalled IT security and control.
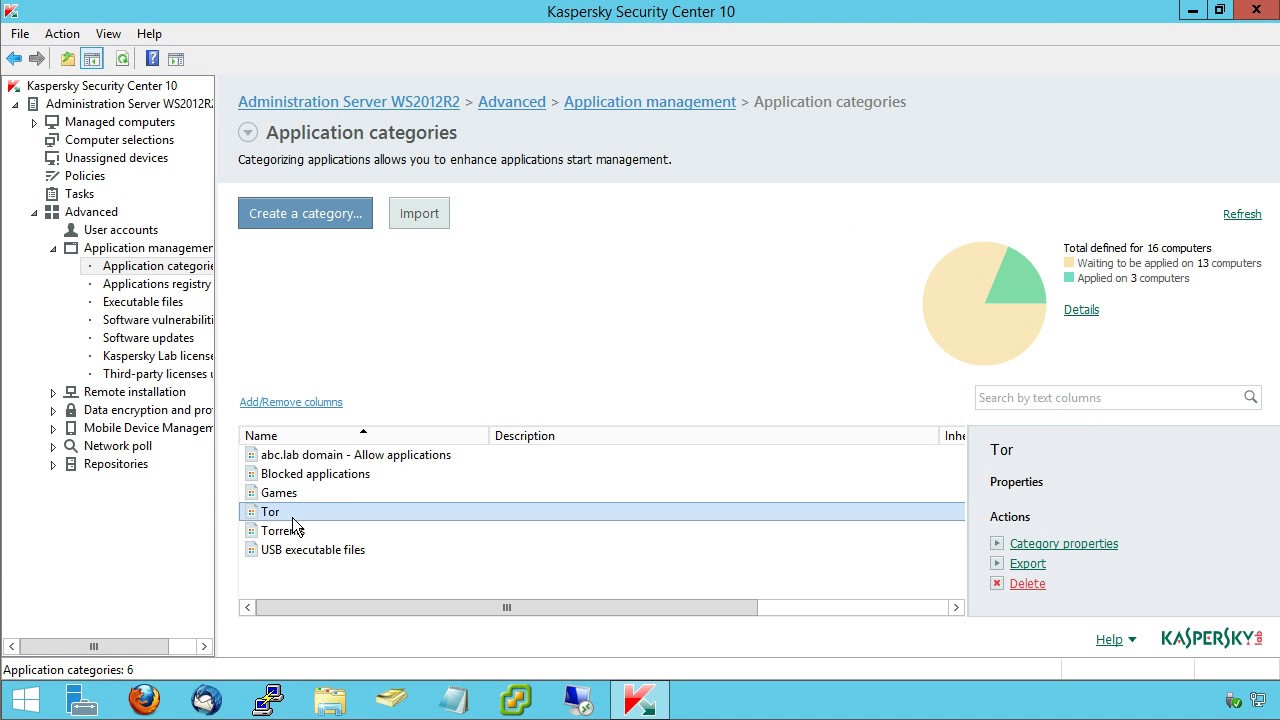
Select the group of managed computers you want to view the policy inheritance for. Users can work securely on any device at any location and your security including Shadow IT Discovery can be managed anywhere anytime from our cloud-based console. The round KSN button in the upper left corner of the window that opens will show the connection status.
In the Inherited policies field click Show. Kaspersky Endpoint Security Cloud protects your business with no need for additional expertise hardware or expenses. In the installation wizard window click Remove.
Clear the Enable password protection checkbox and click OK OK. Kaspersky Endpoint Security Cloud provides a single solution for all your organizations IT security needs - wherever youre heading. It seems to be the case on more components as well for example the File Threat Protection Web Threat Protection and Mail.