Kaspersky Lab Token

Kaspersky Labs comprehensive solution is designed to protect Token Sales projects from various types of threats related to vulnerabilities in smart contracts and web platforms.
Kaspersky lab token. Smart Contract Code Review identifies flaws and undeclared features as well as finds discrepancies between stated in the supporting documentations and smart-contract business logic. Token offering ICO STO projects and cryptocurrency exchanges are. The key will be used in every transform.
The key will be used in every transform. Kaspersky Labs deep threat intelligence and security expertise is constantly. Social media syndication by ImpartnerImpartner.
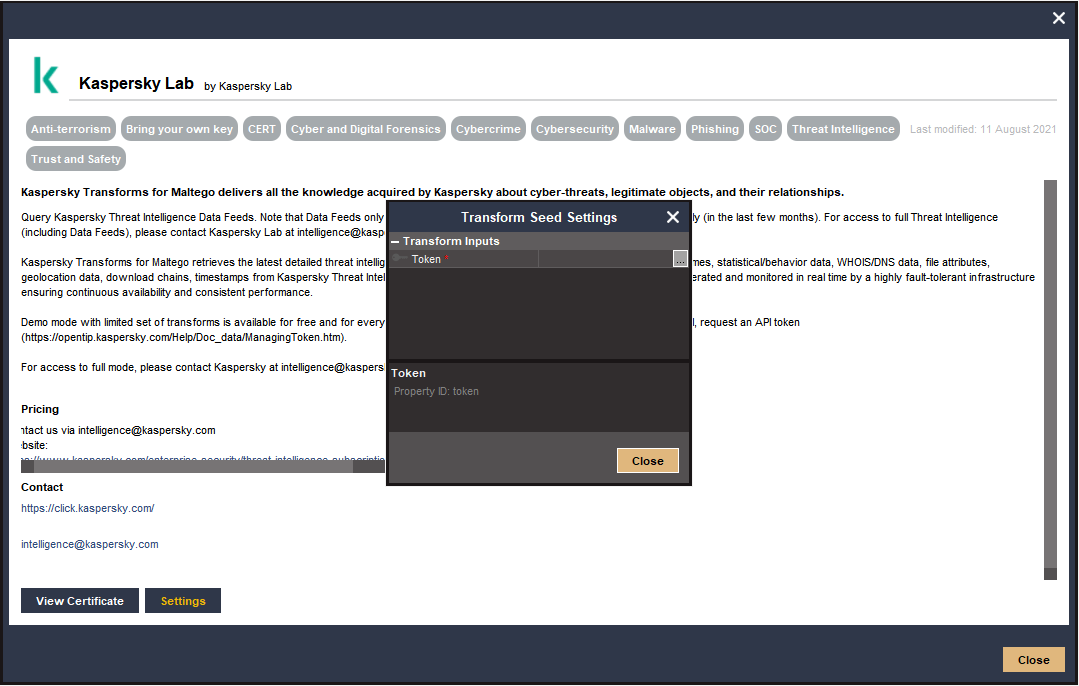
Entering a key token You can also configure the Kaspersky Lab Transform Hub member by clicking the Details button and then clicking the Settings button in the Transform Seed Details dialog box. In the past two years Kaspersky Lab said that its experts have identified a number of such risks and threats such as phishing copies. For token offering projects Kaspersky Lab services include the following.
Kaspersky Lab is a global cybersecurity company which has been operating in the market for over 20 years. Kaspersky Lab and Yandex experts have identified potentially malicious code that pulls more than twenty browser extensions including Frigate Light Frigate CDN and SaveFrom. 2013 - 2021 Kaspersky.
Kasperskys comprehensive solution is designed to provide security for token sales from various types of threats related to vulnerabilities in smart contracts and web platforms. Please enter your email address and password then click the login button. Weprovide thorough code reviews phishing detection incident response and education for staff.
In the Transform Seed Settings dialog box that opens enter the key in the Token field. As an example here you can examine Kaspersky Lab and TokenEx for their overall score 92 vs. Kaspersky Penetration Testing identifies the weak points of your crypto exchange infrastructure with combination of 3 approaches.