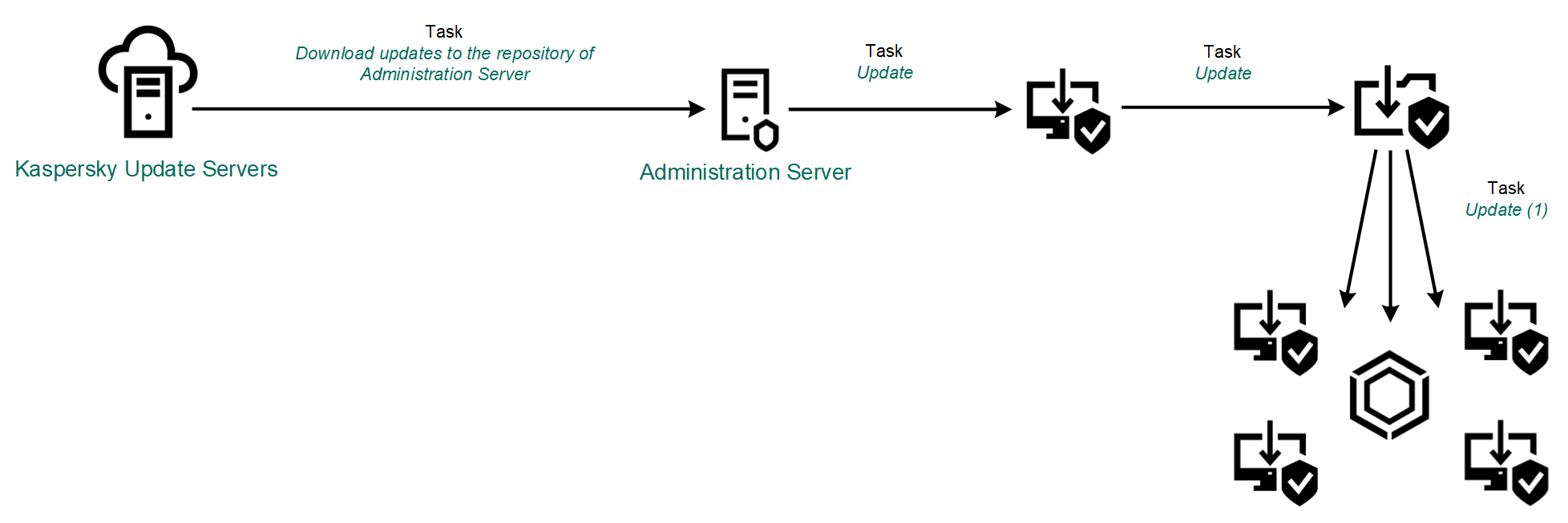
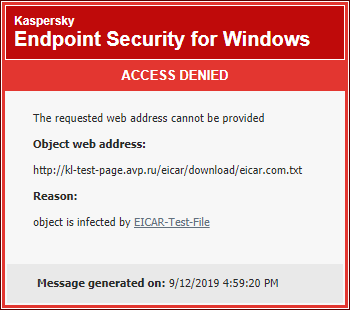
Kaspersky Mac Spoofing Attack
One such substitution involves the use of a fake HTTP header to gain access to hidden content.
Kaspersky mac spoofing attack. Delivering malware link redirection and other means are common in these schemes. MITRE ATTCK Adversarial Tactics Techniques Common Knowledge is a knowledge base describing cybercriminal tactics and techniques based on real-world observations. Were Here to Help.
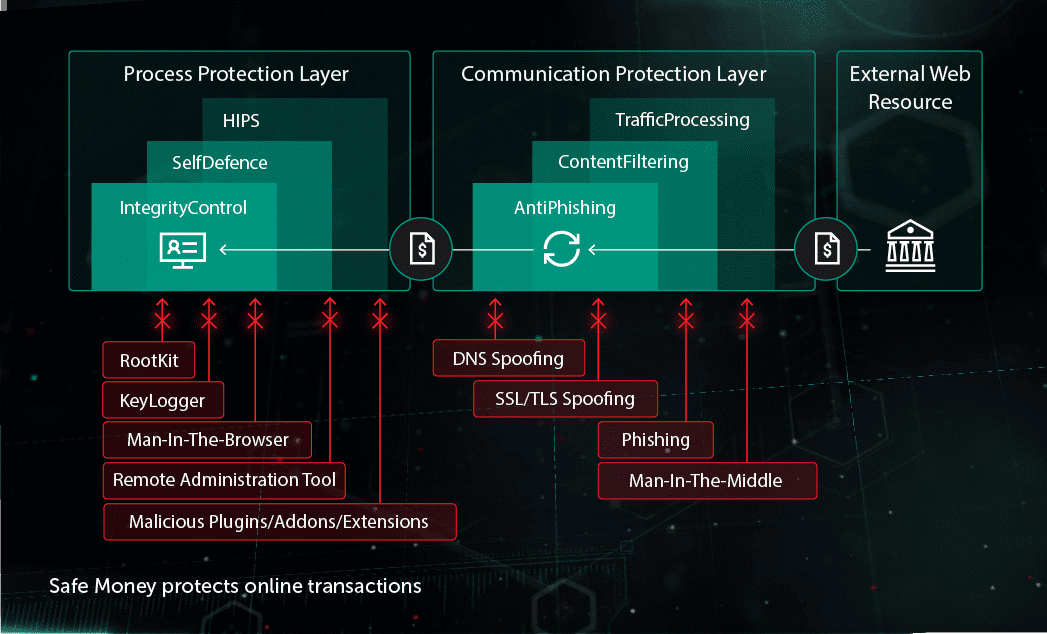
This database is necessary for more accurate routing of packets allowing selective broadcasting to clients on the switch. Where an attacker steps between your web browser and the DNS server to infect both. A man-in-the-middle type cyberattack based on defects in the ARP protocol which is used for resolving MAC addresses by IP and identifying devices in the network.
Among the most widely-used attacks email spoofing often involves things like requests for personal data or financial transactions. Typically a MAC address configured this way remains valid until the device is restarted. It is based on bypassing verification mechanisms through spoof requests that imitate real ones.
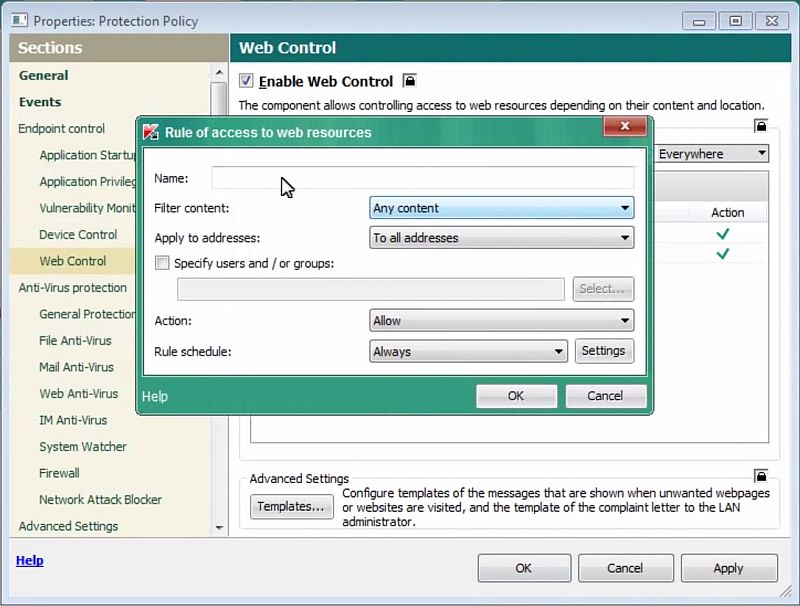
Helping you stay safe is what were about so if you need to contact us get answers to some FAQs or access our technical support team. This provides the intruder valuable details about applications in use and destination host IP addresses. An attack like this might try to exploit weaknesses in a site for any number of other phishing attacks.
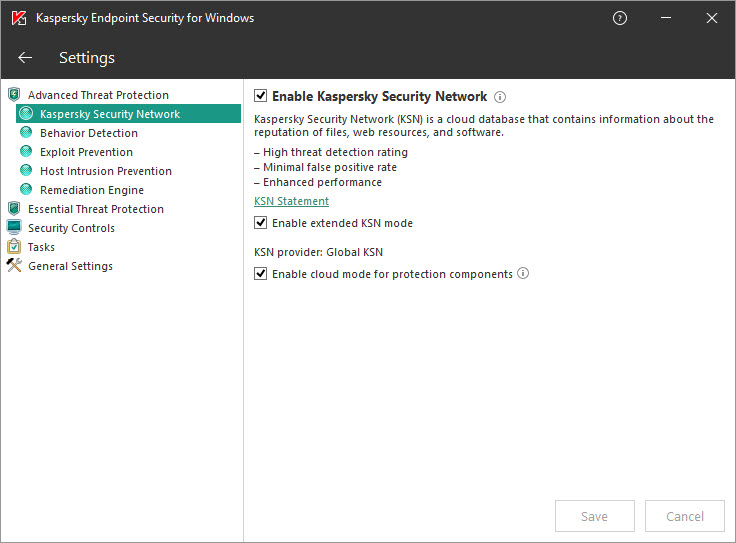
An attacker may also find a vulnerability in the digital environment of a cyber-physical system and exploit it to attack OT processes. Spoofing is a broad term for the type of behavior that involves a cybercriminal masquerading as a trusted user or device to get you to do something beneficial to the hacker and detrimental to you. By installing effective anti-malware software you can defend your mobile devices against Trojans that initiate SMS attacks and unauthorised calls.
I tried here turn on new feature MAC spoofing protection. Methods for DNS Spoofing or Cache Poisoning Attacks. A MAC spoofing attack is where the intruder sniffs the network for valid MAC addresses and attempts to act as one of the valid MAC addresses.